General Networking Topics
This chapter covers general networking concepts listed in the CCIE Security blueprint for
the written exam. The CCIE blueprint lists some example topics that define general
networking, including switching, TCP/IP, routed and routing protocols, PPP, ISDN, and
asynchronous communications.
The CCIE Security written exam contains approximately 50 percent security questions and
approximately 50 percent general networking questions. This chapter prepares you for the
general networking questions. Although the CCIE Security written exam blueprint lists
some specific networking topics, it does not, for example, mention Frame Relay, which
might appear on the exam. This chapter covers many of the listed and a few of the unlisted
general networking topics.
Although these topics are not extensively defined in the blueprint, the CCIE Security
written exam might include topics taken from the CCIE Routing and Switching written
exam blueprint. This chapter endeavors to cover all bases and provide quality test examples
to ensure that you are well prepared to tackle the general networking questions you
encounter in the examination.
This chapter covers the following topics:
•Networking basics—The OSI model, concepts, and functions. Topics include the
seven layers of the OSI model and common examples (TCP/IP).
•Switching and bridging—The process today’s networks use to switch packets and
traditional bridging methods. Virtual LANs, spanning tree, and Ethernet Channel are
discussed.
•Routing IP—The most widely used routed protocol in today’s Internet, IP, and the
routing protocols available on Cisco routers, such as RIP, EIGRP, OSPF, and BGP.
IOS commands and configuration examples demonstrate the power of routing IP on
Cisco routers.
•PPP, ISDN, Frame Relay, IP Multicast, and Async—Two of the most widely used dialup protocols are PPP and ISDN. Frame Relay is covered brie y to ensure that you
have a good understanding of the common terminology used in today’s networks. IP
multicast and async protocols are also covered.
Networking Basics—The OSI Reference Model
This section covers the Open Systems Interconnection (OSI) seven layer model theory and
common examples. CCIE candidates must fully understand and appreciate the model because
almost every routed protocol in use today is based on the architecture of the seven layer model.
The OSI model was developed by a standards body called the International Organization for
Standardization (ISO) to provide software developers a standard architecture to develop proto-
cols (such as IP). For example, the OSI model allows a PC to communicate with a UNIX device.
ISO developed the OSI model in 1984. Layers 1 and 2 are implemented in hardware and Layers 3
The OSI Seven Layer Model
Layer Name Layer Number
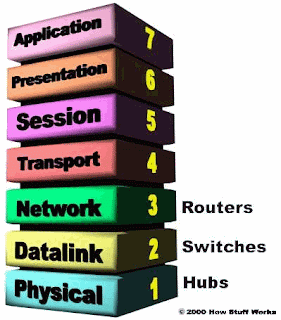
Application Layer 7
Presentation Layer 6
Session Layer 5
Transport Layer 4
Network Layer 3
Data Link Layer 2
Physical Layer 1
The following sections cover each layer and provide protocol examples for each.
Layer 1: The Physical Layer
The physical layer consists of standards that describe bit ordering, bit transmission rates,
connector types, and electrical and other specifications. Information at Layer 1 is transmitted in
binary (1s and 0s). For example, the letter A is transmitted as 00001010. Examples of physical
layer standards include the following:
• RS-232
• V.24
• V.35
• RJ-45
• RJ-12
Layer 2: The Data Link Layer
The data link layer focuses on getting data reliably across any particular kind of link. Flow
control and error notifications are also functions of the data link layer. The data link layer
applies to all access methods, whether they are LAN or WAN methods. Information being
processed at this layer is commonly known as frames.
The IEEE further complicated matters by subdividing the data link layer into to sublayers: the
Logical Link Control (LLC) sublayer and the MAC sublayer.
IEEE Sublayers Versus ISO Definitions
IEEE 802 Definition
ISO Standard
Logical Link Control, LLC
Data Link Layer
MAC Sublayer
Physical Medium (Layer 1)
The LLC sublayer manages and ensures communication between end devices, and the Mac
sublayer manages protocol access to the physical layer.
Examples of data link frame types include the following:
•ISDN
•SDLC
•HDLC
•PPP
•Frame Relay
•Ethernet Version II
•Spanning tree protocol
•NetBEUI
Layer 3: The Network Layer
The network layer determines the best path to a destination. Device addressing, packet
fragmentation, and routing all occur at the network layer. Information being processed at
this layer is commonly known as packets. Examples of network layer protocols include the
following:
• Internet Protocol (IP)
• Open Shortest Path First (OSPF)
• Cisco’s EIGRP routing protocol
Routing protocols (OSPF, EIGRP, and BGP, for example) provide the information required to
determine the topology of the internetwork and the best path to a remote destination. A routed
protocol is one that is transported by a routing protocol (such as RIP). For example, IP is a
routed protocol that can be advertised by a number of routing algorithms, such as RIP, OSPF,
and BGP.
Connection-oriented and connectionless protocols are commonly used terms to describe Layer 3
and 4 (lower layers of the OSI model) protocols, such as IP or TCP.
A connection-oriented protocol, such as TCP, ensures delivery of all information, whereas a
connectionless protocol, such as IP, only packages the data and sends it without guaranteeing
delivery. Connection-oriented protocols exchange control information (also called Handshake)
before transmitting data. A telephone call can be considered a connection-oriented service
because the call is established before conversation can take place, much the same way that TCP
sets up a data connection before data is sent. FTP is another example of a connection-oriented
protocol. IP is an example of connectionless service.
The transport layer is responsible for segmenting upper-layer applications and establishing end-
to-end connections between devices. Other transport layer functions include providing data
reliability and error-free delivery mechanisms. Information being processed at this layer is
commonly known as segments. Examples of transport layer protocols include the following:
• Transmission Control Protocol (TCP)
• Real-time transport protocol (RTP)
• User Datagram Protocol (UDP)
Layer 5: The Session Layer
The session layer performs several major functions, including managing sessions between
devices and establishing and maintaining sessions. Examples of session layer protocols include
the following:
•Database SQL
•NetBIOS Name Queries
• H.323 (Supports video as well; it is the packet switch voice standard)
• Real Time Control Protocol
Layer 6: The Presentation Layer
The presentation layer handles data formats and code formatting. The layer’s functions are
normally transparent to the end user because this layer takes care of code formats and presents
them to the application layer (Layer 7), where the end user can examine the data. Examples of
presentation layer protocols include the following:
•GIF
•JPEG
•ASCII
•MPEG
•TIFF
•
•HTML
Layer 7: The Application Layer
The application layer is closest to the end user, which means that the application will be
accessed by the end user. This layer’s major function is to provide services to end users.
Examples of application layer services include the following:
• File Transfer Protocol (FTP)
• Telnet
•
• Trace route
• SMTP
• Mail clients
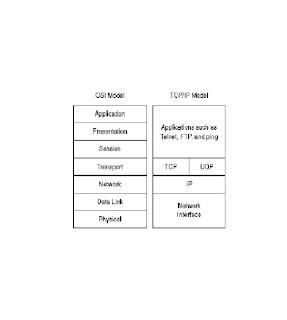
TCP/IP and OSI Model Comparison
TCP/IP is the most widely used networking protocol and is often compared to the industry-
defined OSI model.
Figure 2-2 displays the TCP/IP model in relation to the OSI model and where the protocol suite
of TCP/IP lines up with the ISO standard. This comparison is provided to demonstrate that
TCP/IP does not exactly conform to the OSI model. For example, the TCP/IP model has no
Layer 5 or 6.
Example of Peer-to-Peer Communication
Each layer of the OSI or TCP model has its own functions and interacts with the layer above and
below it. Furthermore, the communication between each layer’s end devices also establishes
peer-to-peer communication; this means that each layer of the OSI model communicates with
the corresponding peer.
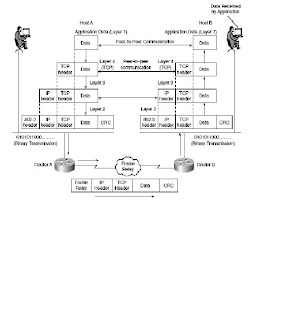
Consider the normal communication that occurs between two IP hosts over a wide-area network
(WAN) running Frame Relay,.
|
|
The data from one (Host A) is encapsulated inside a TCP header and passed down to Layer 3
(the IP layer) for address configuration, where an IP header is also added. Information included
here is the source IP address and destination address. Layer 3 (the network layer) passes the
data to the local router acting as the gateway via the Ethernet connection in raw binary.
Router A strips the 802.3 header and encapsulates the IP, TCP, and data in a Frame Relay packet
for delivery over the WAN. A CRC is added here to ensure the packet is not corrupted over
the WAN. Frame Relay is connectionless so, if an error occurs, it’s up the to upper layers to
retransmit; Frame Relay will not retransmit the packet. Similarly, HDLC (Layer 2 protocol)
is connectionless and depends on upper layers to resubmit damaged data packets. PPP
(connection-oriented), on the other hand, resubmits packets damaged in transmission over
the WAN.
Router B receives the Layer 2 frames and strips the Frame Relay header/CRC and encapsulates
the IP, TCP, and data frame back into an 802.2 header (with its own CRC; Ethernet checks only
for errors and cannot repair them; once more, upper layers, such as TCP, ensure data delivery)
for binary transmission across the Ethernet to Host B. The data is passed up the layers through
IP, TCP, and finally to the application, where the application layer reads and acts upon the data.
The good news for security candidates is that Token Ring and legacy technologies are not
covered in the written exam, so this chapter concentrates only on Ethernet switching. Before
covering switching, the next section summarizes the evolution of Ethernet so that you are aware
of the standards that have developed since Xerox first introduced Ethernet.
Ethernet Overview
Ethernet networks are based on a development made by Xerox, Digital, and Intel. The two
versions of Ethernet are commonly referred to as Ethernet I and Ethernet II (or version 2).
Ethernet uses Carrier Sense Multiple Access Collision Detection (CSMA/CD) to transmit
frames on the wire. In an Ethernet environment, all hosts can transmit as long as no other
devices are transmitting. CSMA/CD is used to detect and warn other devices of any collisions,
and colliding stations will use a back off algorithm and wait a random amount of time before
trying again. Colliding devices send a jam signal to advise all stations that a collision has
occurred. When a jam signal is sent (a jam signal is detected by all devices because the voltage
is that of the combined colliding devices), all stations also stop transmitting. A device will
attempt to transmit up to 16 times before a user is notified of the collisions; typically, an
application error will inform the user that data could not be delivered. Microsoft’s famous
words are “Network is busy.”